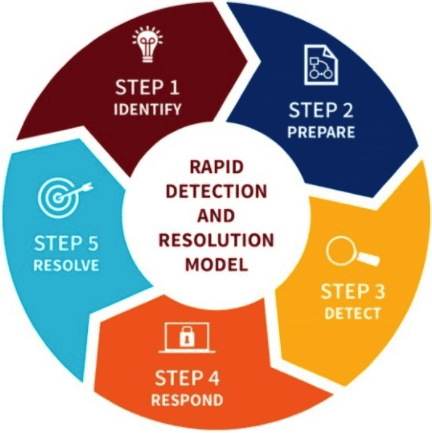
Incident Management
3RT Networks incident response methodology is a critical element to our customer experience. By following a structured approach when responding to customer incidents and service requests we can ensure a consistent and timely resolution for the customer.
Cyber Security Incident Management
Identifying, managing, recording, and analyzing security threats or incidents in real-time, cyber security incident management provides a robust and comprehensive view of any security issues within an IT infrastructure. 3RT Networks works with our customers to develop a security incident management plan and the tools to effectively handle these types of security events if they should arise.
Identify the threat or incident and formulate a response strategy.
Manage the incident with consistent status tracking, action verification, and communication with stakeholders.
Leverage cyber security tools and logs to identify the scope of the incident and isolate patterns. Proper forensics can be used in a remediation plan or reverse engineering of malware.
Actions taken to quarantine or stop the ability for the intrusion to cause further harm.
Removal and disposal of all threats left by incident including malware, applications, and artifacts.
Carefully planned communication in the wake of a breach can play a major role in maintaining an organization’s reputation and financial impact. 3RT Networks’ Crisis Team resources can assist or facilitate this communication depending on what the customer requires, not relying on a one-size-fits-all approach.
Why 3RT Networks?
Companies Trust 3RT Networks